Featured
Table of Contents
- – Is It Safe To Use Vpn In Combination With Tor B...
- – Tor Vs Vpn: Which One Is Better? - The World's...
- – Vpn Vs Tor Vs Proxy Vs Firewall: Full Comparis...
- – Tor Vs Vpn: What They Do And Which Is Better?
- – Tor And Vpn: Everything You Need To Know
- – Tor Vs Vpn - What Are They And Which Is Better?
- – Tor Vs Vpn: Which One Should You Use?
- – Tor Vs Vpn: What's The Difference And When T...
Is It Safe To Use Vpn In Combination With Tor Browser?

Standard route tracing, which can quickly be done online free of charge, will reveal your real IP address and area. If you're doing anything questionable, then your internet service provider, federal government or anybody else who can access your stream of information can see it. Even so, proxies have their location. There are various types of servers you can utilize depending on the traffic you want to conceal.
HTTP proxies are implied specifically for internet traffic. You go into the IP address of the proxy you want to connect to in your browser's settings and traffic will be routed through that server.

There's no file encryption outside what you supply and the traffic load and speed are up in the air. Plus, SOCKS proxy servers have more overhead, so they are normally slower than HTTP.
Tor Vs Vpn: Which One Is Better? - The World's Best And Worst
Instead, they assist companies scrape data from websites. Most corporations blocklist IP addresses originating from other businesses, so those organizations need to utilize proxy servers if they wish to get that data. That's the real purpose of a paid proxy, and it's no more secure than a complimentary proxy server.
A VPN connection keeps your online activity completely confidential. When your encrypted connection reaches the VPN server, it gets decrypted and sent again to its destination. The website reacts to your request and sends out the reply back to the VPN server, which then secures that reply and sends it to you, where it gets decrypted only when it reaches your device.
We'll talk about totally free VPN services in a bit, however for now, suffice it to state that if you require a VPN, you need to utilize a paid one. The extra cost features additional security, reliability and functions. VPNs can bypass the harshest geoblocks and let you gain access to restricted content throughout the globe.
Vpn Vs Tor Vs Proxy Vs Firewall: Full Comparison 2021
VPN services provide the best balance of security and speed for P2P connections something proxy servers and Tor battle with. If you want to consistently unclog online content, you ought to utilize a fast and protected VPN like Express, VPN.
While they're meant to safeguard your privacy, a VPN supplier can see your web traffic and, in some cases, log it. Companies such as IPVanish have actually been caught red-handed logging user data and handing it to the federal government.

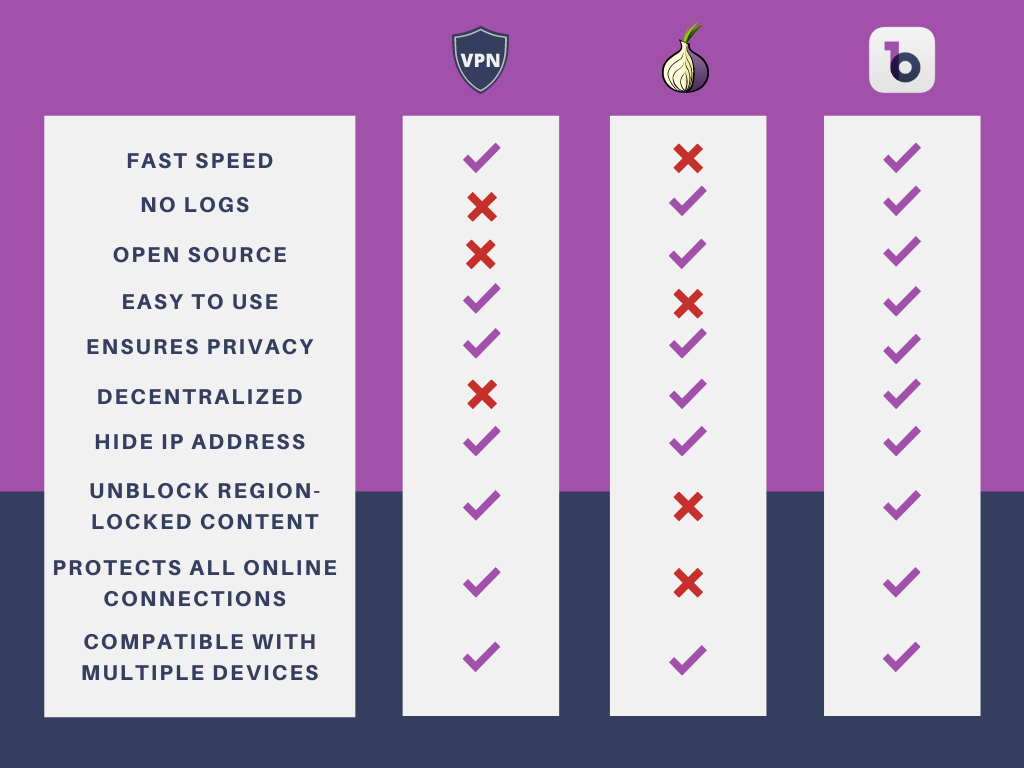
The greatest disadvantage is that a good VPN, in practically every case, will cost cash. There are totally free choices, however as you can see in our worst free VPNs guide, they include unexpected effects. There are uncommon exceptions to this, like Windscribe, Proton, VPN and Tunnel, Bear. In our viewpoint, Windscribe is the finest totally free VPN around, as you can check out in our Windscribe review.
Tor Vs Vpn: What They Do And Which Is Better?
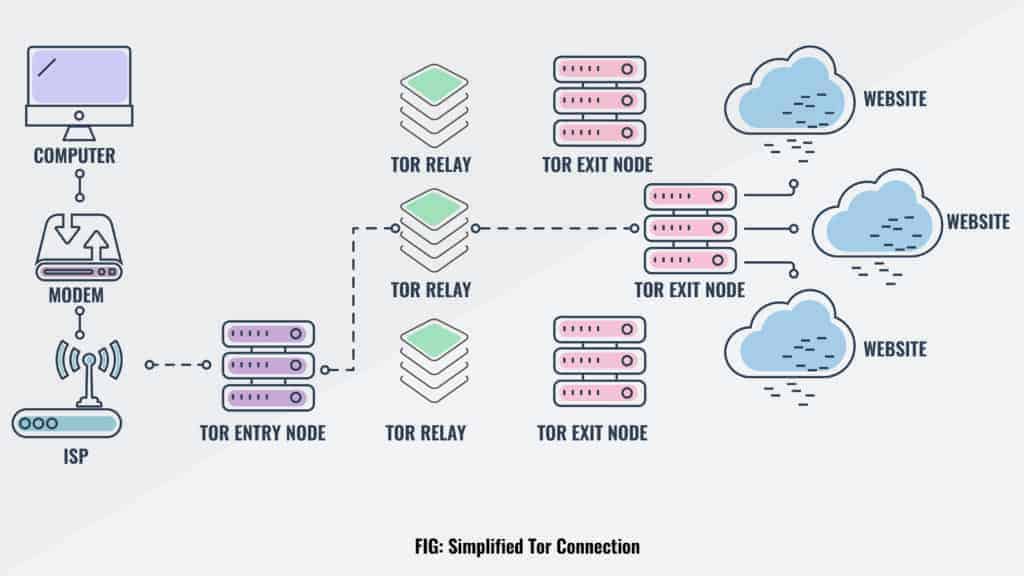
Traffic on the network is secured as well, so it's partially safer than a proxy. Like proxy servers, Tor exit nodes (the last server your connection bounces off of) are recognizable.
Massachusetts Institute of Technology scientists, for example, have actually been able to break Tor without cracking the file encryption it utilizes. The standard property is that somebody who's snooping on a Tor connection can utilize traffic fingerprinting to determine what content a user is accessing. The information can be kept an eye on and the packets counted to figure out where the connection is originating from and where it's going.
Tor doesn't work for P2P connections and is much slower than a proxy or VPN. Proxy servers are convenience- and speed-focused services that are suitable for bypassing fundamental geoblocks, and Tor focuses on brute-forcing privacy at the cost of huge amounts of speed.
Tor And Vpn: Everything You Need To Know
Really, the only disadvantage is that you have to pay for a VPN. There's actually no contest in between Tor, a VPN and proxy server the VPN always wins. For many people, a VPN is the very best option, however that should not come as much of a surprise. A VPN connection is encrypted, secure and quick.
, and proxies are a fast and low-cost option for standard IP masking. As a well-rounded solution, however, VPNs are best.
Let us understand if you liked the post. That's the only way we can improve. Yes No.
Tor Vs Vpn - What Are They And Which Is Better?
Something failed. Wait a minute and attempt once again Attempt again.
Massachusetts Institute of Innovation researchers, for instance, have actually been able to break Tor without cracking the file encryption it utilizes. The basic premise is that someone who's snooping on a Tor connection can use traffic fingerprinting to determine what material a user is accessing. The data can be kept an eye on and the packets counted to determine where the connection is originating from and where it's going.
Tor doesn't work for P2P connections and is much slower than a proxy or VPN. Proxy servers are convenience- and speed-focused solutions that are appropriate for bypassing basic geoblocks, and Tor focuses on brute-forcing anonymity at the expense of huge quantities of speed.
Tor Vs Vpn: Which One Should You Use?
Truly, the only disadvantage is that you have to spend for a VPN. There's really no contest in between Tor, a VPN and proxy server the VPN constantly wins. For many people, a VPN is the very best option, however that shouldn't come as much of a surprise. A VPN connection is encrypted, secure and quick.
, and proxies are a quick and low-priced solution for basic IP masking. As an all-around solution, though, VPNs are best.
Let us understand if you liked the post. That's the only method we can enhance. Yes No.
Tor Vs Vpn: What's The Difference And When To Use Each
Something went incorrect. Wait a minute and try again Attempt once again.
Table of Contents
- – Is It Safe To Use Vpn In Combination With Tor B...
- – Tor Vs Vpn: Which One Is Better? - The World's...
- – Vpn Vs Tor Vs Proxy Vs Firewall: Full Comparis...
- – Tor Vs Vpn: What They Do And Which Is Better?
- – Tor And Vpn: Everything You Need To Know
- – Tor Vs Vpn - What Are They And Which Is Better?
- – Tor Vs Vpn: Which One Should You Use?
- – Tor Vs Vpn: What's The Difference And When T...
Latest Posts
The Best Mobile Vpns Of 2023
The Best Vpn Of 2023 - Cnn Underscored
The 5 Best Android Vpn Apps Reviewed (*Updated 2023)
More
Latest Posts
The Best Mobile Vpns Of 2023
The Best Vpn Of 2023 - Cnn Underscored
The 5 Best Android Vpn Apps Reviewed (*Updated 2023)